What Is xmlrpc.php In WordPress And How To Disable It
In the dynamic and ever-evolving world of website management, WordPress has emerged as a powerful and versatile platform. It empowers millions of individuals, businesses, and organizations to create and maintain their online presence with ease. However, with this popularity comes a unique set of challenges, including the need to safeguard your website from potential security threats. One often-discussed component of WordPress, which can be a source of concern for site owners, is the enigmatic “xmlrpc.php” file.
XML-RPC, or Extensible Markup Language Remote Procedure Call serves as a protocol crafted specifically for WordPress, offering a standardized means of communication between diverse systems. While this feature can be beneficial for some users, it also poses security risks, making it a topic of much debate and concern within the WordPress community.
This article aims to demystify xmlrpc.php in WordPress by exploring its purpose, its potential vulnerabilities, and most importantly, how to disable it if you decide it’s necessary for your website’s security. So, let’s delve into the world of xmlrpc.php in WordPress and equip you with the knowledge to make informed decisions about its use on your website.
What Is xmlrpc.php on WordPress?
XML-RPC in the context of WordPress is a fundamental feature that enables remote communication and interaction between different software applications or systems over the internet. At the heart of this functionality is the xmlrpc.php file, a crucial script that plays a pivotal role in how external applications and services can interface with your WordPress website.
One of the primary functions of xmlrpc.php is to facilitate remote publishing on a WordPress site. This means that it allows users to create, edit, and manage various content types, such as blog posts and pages, without needing to access the WordPress dashboard directly. This feature is particularly beneficial for individuals, bloggers, or content creators who prefer to use specialized writing or editing tools, mobile apps, or other external software to produce and update content on their WordPress websites.
Furthermore, xmlrpc.php extends beyond remote publishing capabilities. It also enables external software to perform a range of content management tasks. For example, it allows for the manipulation of categories, tags, comments, and user accounts. This functionality is valuable for site owners who want to streamline content management or use third-party tools for these purposes while keeping their WordPress site as the central hub of their online presence.
In addition to content management and remote publishing, xmlrpc.php is integral to the functioning of pingbacks and trackbacks in WordPress. WordPress uses these mechanisms to notify other websites when your site links to their content. Through xmlrpc.php, your site can send and receive these notifications, thereby facilitating a broader network of connections and interactions across the web.
Why Was xmlrpc.php Created and How Was It Used?
The utilization of XML-RPC in the context of WordPress dates back to the platform’s early stages, a time when it wasn’t even known as WordPress.
During the nascent years of the internet, creating and publishing content online was considerably more challenging and time-consuming, primarily due to sluggish internet connections. Instead of composing directly within web browsers, individuals often authored their content offline and then manually transferred it to the web, a process far from efficient.
To address this issue, a solution emerged in the form of offline blogging clients, allowing users to craft their content offline and subsequently connect to their blogs for publication. This connection was established through XML-RPC. As the framework of XML-RPC became established, early applications leveraged this connection to enable individuals to access their WordPress sites from various devices.
Initially, XML-RPC was not enabled by default, and it required manual configuration. It was only with the advent of WordPress 2.6 that the dashboard introduced a feature allowing users to easily enable or disable XML-RPC as needed.
Significant changes occurred with the arrival of WordPress 3.5 and the introduction of the WordPress mobile app. At this juncture, XML-RPC was enabled by default, simplifying the process for users to connect to their sites. The option to enable or disable XML-RPC was subsequently removed from the dashboard, reflecting the platform’s evolving approach to this essential communication protocol.
Reasons to disable xmlrpc.php on WordPress:
Disabling xmlrpc.php on a WordPress site is a security measure that site owners can consider for a variety of reasons. While xmlrpc.php offers useful functionalities, some scenarios may warrant its disabling. If you rely on these functionalities or use external applications that require XML-RPC, you may want to explore alternative methods to secure and control access to xmlrpc.php rather than disabling it outright.
Brute Force Attacks:
Brute force attacks involve hackers trying numerous username and password combinations to gain unauthorized access to a website’s backend. Sites with weak admin passwords and no multi-factor authentication are at higher risk.
Hackers employ automated tools to identify valid usernames for a website. With this data, they can exploit the xmlrpc.php file, executing brute force attacks by sending multiple password combinations. If a site’s security is lacking, hackers can bypass reCaptchas and login limits, potentially gaining unauthorized access, and posing a significant security threat.
Hence, if your WordPress version relies on the REST API for external communication, consider disabling XML-RPC to enhance security.
DDoS Attacks:
DDoS attacks can overwhelm your server with a flood of simultaneous requests, rendering it inaccessible. In the attack’s initial stages, hackers pinpoint a target page and verify the presence of the xmlrpc.php file through a specific request. Once confirmed, they initiate a barrage of pingback requests from a network of compromised websites. In many cases, hackers can automate this process using specialized code, allowing them to flood the target site with numerous pingback requests.
To enhance security and reduce the risk of DDoS attacks, disabling xmlrpc.php can be a prudent step in maintaining the integrity of your WordPress website.
Plugin or Theme Compatibility:
The xmlrpc.php file in WordPress can potentially cause compatibility issues with certain plugins and themes. While this script is a fundamental part of the WordPress core and plays a crucial role in external communication, some older or less-maintained plugins and themes may not be fully compatible with it. In such cases, conflicts may arise, leading to unexpected errors, broken functionalities, or even site crashes.
It’s crucial for WordPress site owners to ensure that their plugins and themes are up-to-date and well-maintained to minimize these compatibility concerns. In some instances, if a plugin or theme is causing conflicts with xmlrpc.php, it may be necessary to seek alternative solutions or consider disabling xmlrpc.php, although this should be done cautiously, as it can impact other functionalities and interoperability with external services.
Content Theft Prevention:
Disabling the xmlrpc.php file in WordPress can help mitigate content theft to some extent. This is because content scrapers can exploit xmlrpc.php as a potential entry point. By disabling it, you make it more challenging for malicious actors to access and duplicate your content via automated means.
However, it’s important to understand that content theft can still occur through other methods, such as manual copying and pasting or web scraping tools that don’t rely on xmlrpc.php. To enhance content protection, it’s advisable to use other security measures like employing anti-scraping plugins, setting appropriate access permissions, and regularly monitoring your site for unauthorized use of your content.
How to check if xmlrpc.php is running on a website or not?
Before considering disabling XML-RPC, it’s essential to verify the status of xmlrpc.php on your website. To check if xmlrpc.php is running on a website, you can perform the following steps:
In your web browser, go to your website’s URL, for example, “https://www.yourwebsite.com.”
Append “/xmlrpc.php” to the end of your website’s URL, creating a new URL like: “https://www.yourwebsite.com/xmlrpc.php.”
Press Enter or navigate to this URL.
If xmlrpc.php is active and accessible, you will typically see an XML-RPC response, which might include an error message or information about the xmlrpc.php file.
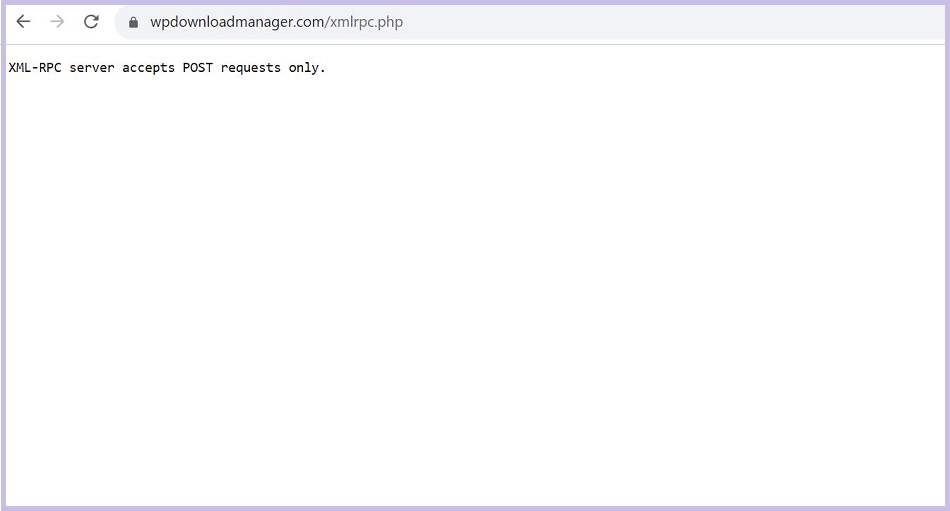
If you’ve got the message “XML-RPC server accepts POST requests only” it means XML-RPC is enabled on your site. It is active, visible, working, and a possible vulnerability on your site.
How To Disable xmlrpc.php?
Disabling xmlrpc.php in WordPress can be achieved through various methods. Here are a couple of common approaches:
Using a Security Plugin:
Disabling XML-RPC on your WordPress site is a straightforward process. You can achieve this by following these steps:
- Access your WordPress dashboard and navigate to the “Plugins” section.
- Click on “Add New” to explore and search for plugins.
- In the search bar, type “Disable XML-RPC-API” or “Disable XML-RPC” and locate the corresponding plugin.
- Install the plugin.
- After installation, activate the plugin. It will automatically apply the necessary code to deactivate XML-RPC.
Editing the .htaccess File:
You can also disable xmlrpc.php by editing your site’s .htaccess file. Here’s how:
- Access your website’s files using an FTP client or a file manager provided by your hosting provider.
- Locate the .htaccess file in your site’s root directory.
- Open the .htaccess file in a text editor.
- Add the following lines to the file:
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>- Save the .htaccess file and upload it back to your server.
Using Custom Functions (Advanced):
If you’re comfortable with editing your theme’s functions.php file, you can add custom code to disable xmlrpc.php. Here’s an example:
- In your WordPress dashboard, go to “Appearance” and select “Theme Editor.”
- On the right-hand side, find your theme’s functions.php file and click to edit it.
- Add the following code at the end of the file:
// Disable XML-RPC
add_filter('xmlrpc_enabled', '__return_false');- Save your changes.
After implementing any of these methods, xmlrpc.php should be effectively disabled on your WordPress site. Remember it’s important to exercise caution when disabling XML-RPC since some of your existing plugins may rely on certain XML-RPC functionalities. Complete deactivation might lead to plugin conflicts or disrupt specific elements of your website’s functionality. Always test your site thoroughly after making such changes to ensure everything continues to work as expected.
When Do You Need To Enable xmlrpc.php File?
In certain scenarios, it’s necessary to enable xmlrpc.php on your WordPress site, and completely disabling it may not be the ideal approach. Here are some instances where enabling xmlrpc.php is warranted:
REST API Absence:
If you’re not utilizing the REST API and need to facilitate communication between your WordPress site and other systems, xmlrpc.php becomes a viable option, although not the recommended one.
Inability to Update WordPress:
When you cannot update your WordPress installation to version 4.4 or higher, potentially due to hosting restrictions or theme and plugin incompatibility, xmlrpc.php can serve as a temporary solution. However, addressing the root causes of these issues, such as considering a different hosting provider or updating themes and plugins, is advisable for long-term site health.
External Application Limitations:
If you’re working with an external application that lacks access to the WP REST API but can communicate via XML-RPC, it might necessitate the temporary use of xmlrpc.php. However, it’s recommended to explore options for updating the application or transitioning to a REST-compatible alternative in the long run.
Conclusion:
xmlrpc.php in WordPress serves as a valuable component that enables remote communication between a WordPress site and external systems. However, due to its history of security vulnerabilities, some site owners might opt to disable or restrict access to this file to enhance their site’s security. Balancing between security and the required functionalities is key when considering whether to disable xmlrpc.php on a WordPress site. Ultimately, understanding xmlrpc.php and making informed choices regarding its use is vital for maintaining a secure and efficient WordPress environment.
For more articles on online security and privacy check our Blog section. Also, don’t forget to follow our Facebook page and subscribe to our YouTube channel.